From Risk Assessment to Employee Training Top Six Essential Cybersecurity Best Practices for the Pharmaceutical Industry

In today’s digital world, cybersecurity is more important than ever before, especially in the pharmaceutical industry. Pharmaceutical companies store and process highly sensitive information, such as confidential research data, patient records and intellectual property. A data breach or cyberattack can cause immense financial and reputational damage. Therefore, it is essential for pharmaceutical companies to implement effective cybersecurity measures to protect their assets.
The cost of a data breach for the pharmaceutical industry can be significant and varies depending on the scope and severity of the breach. According to the IBM Cost of a Data Breach Report 2022 (1), the average cost of a data breach for a pharmaceutical company is $5.01 million. Moreover, the average breach in healthcare increased by nearly USD 1 million to reach USD 10.10 million from March 2021 to March 2022. Breach costs to the healthcare industry have been the most expensive industry for 12 years, increasing by 41.6% since the 2020 report. Financial organizations had the second highest costs — averaging USD 5.97 million. This illustrates that the healthcare and pharmaceutical industries are attractive markets for hackers. Thus, they require cybersecurity protection to avoid disruptions to the business, which compromises the ability to innovate and provide new treatments to society (Figure 1).
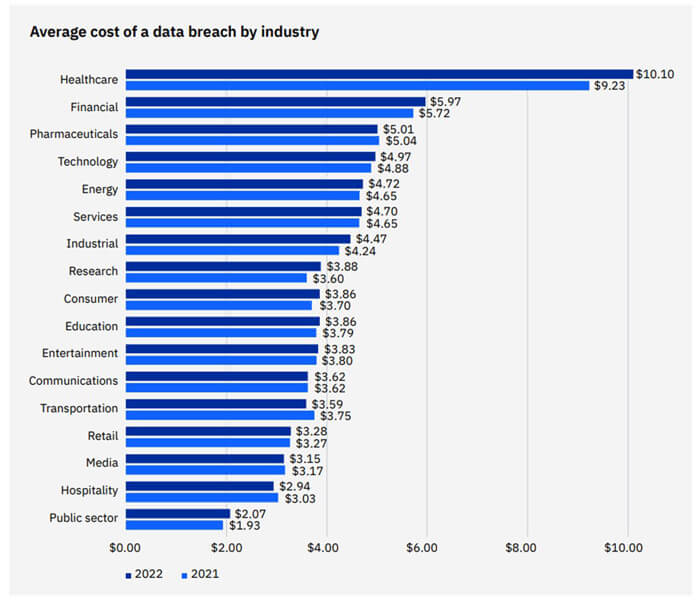 Figure 1 From IBM Cost of a Data Breach Report 2022
Figure 1 From IBM Cost of a Data Breach Report 2022
Conduct a Comprehensive Risk Assessment
A comprehensive risk assessment is the foundation of any effective cybersecurity program. It helps companies identify potential threats and vulnerabilities, assess the value of their assets and evaluate the potential impact of a cyberattack. A risk assessment should include:
- An inventory of all systems and data
- A clear understanding of the supported processes
- A review of access controls and permissions
- An evaluation of existing security measures
The findings of a risk assessment can help companies develop a cybersecurity strategy that addresses the identified risks in the context of people, technologies and processes. Typically, the risk assessment requires multiple interactions with different stakeholders, including but not limited to system owners, product owners, developers, subject matter experts from information technology (IT) or operational technology (OT) departments, Information Security Team members and vendors. The outcome is the creation of a methodology on how the risk assessment should be executed, along with the rates of probabilities, impact, risk level and the composition of a mitigation plan. Table 1 provides an example of a risk-assessment table.
Table 1 Sample Risk-Assessment Table| Asset | Threat | Probability | Impact | Risk Level | Possible Mitigation |
|---|---|---|---|---|---|
| Customer Data | Cyberattack on customer data stored in the company’s database | High | High | High | Encrypt customer data, implement multifactor authentication, and conduct regular security-awareness training for employees |
| Manufacturing Equipment | Human error leading to equipment malfunction or failure | Medium | Medium | Medium | Implement proper training and safety protocols for employees, conduct regular maintenance and inspections on equipment, and consider backup or redundancy measures |
| Intellectual Property | Insider threat, such as an employee stealing or sharing confidential information with unauthorized parties | Low | High | High | Implement access controls, regularly monitor and audit employee activity, conduct background checks on employees, and conduct security-awareness training for employees |
Developing an effective risk assessment requires expertise and experience to create a comprehensive mitigation plan that addresses potential threats. Fortunately, cybersecurity teams have created resources to help organizations deal with cyber-threat scenarios. These resources can suggest improvements to existing controls or propose new controls to mitigate threats. Some of these helpful organizations can be easily accessed online:
- OWASP Top 10 provides instructions on security software development best practices (2)
- MITRE ATT&CK contains adversary tactics from real-world observations (3)
- Cybersecurity and Infrastructure Security Agency (CISA) diligently tracks and shares information about the latest cybersecurity risks, attacks and vulnerabilities (4)
Implement Multilayered Access Controls
Access controls are crucial for maintaining the security of sensitive data and systems within the pharmaceutical industry. To prevent unauthorized access, companies should implement multilayered controls that limit access to sensitive information on a need-to-know basis. This can include using password-protected accounts with multifactor authentication and role-based permissions.
Limiting access to sensitive information is a fundamental step companies can take to mitigate the risk of data breaches and other security incidents. However, it is equally important to ensure access controls are properly managed and enforced. Regular monitoring and auditing of access to all sensitive data and systems can help to identify potential security breaches and ensure compliance with access policies. Nonetheless, to accurately track access, a network time-protocol server is critical for ensuring that the appropriate timestamp is used when generating logs for access control in the pharmaceutical industry. This allows companies to accurately record and analyze access data, detect anomalies, and respond quickly to security incidents. By implementing these best practices, pharmaceutical companies can significantly improve their cybersecurity posture and safeguard their valuable assets.
Implementing effective access controls can be challenging. Consequently, it is important to provide regular training and awareness programs for employees to ensure that they understand the importance of access controls and are equipped with the knowledge and skills needed to use them effectively.
Use Strong Encryption
Encryption is a critical component of any cybersecurity program. Pharmaceutical companies should use strong encryption algorithms, such as Advanced Encryption Standard, to protect sensitive data both at rest and in transit. Encryption should be used for email, file transfers and storage. Additionally, companies should ensure that encryption keys are properly managed, and access to sensitive data is strictly controlled.
A risk-based evaluation of key management in encryption is essential for pharmaceutical companies to ensure that no harm is caused in the long term, especially if the key is under vendor management. For instance, assessing whether the key can still be used to read the encrypted content after 10 years or more is important.
Implement Regular Software Updates
Cybercriminals often exploit vulnerabilities in outdated software and systems. Consequently, pharmaceutical companies should ensure that all their systems and software are up to date and that security patches are applied promptly. This includes not only the company’s servers and workstations but also any OT systems that are used in the production or testing of pharmaceutical products. Companies should also conduct regular vulnerability assessments to identify potential security risks and take prompt action to address them. The challenge lies in the lack of understanding and alignment between IT and OT on how to conduct patching. While IT focuses more on the confidentiality and integrity aspects of the patching process, OT concentrates on safety, reliability and performance. As a result, OT systems may vary in their ability to apply updates quickly to avoid any disruptions or impacts on production.
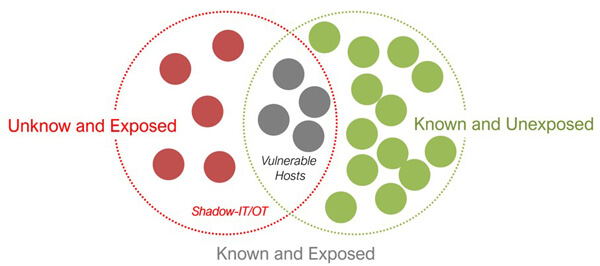 Figure 2 Unknown and exposed zones in shadow-IT or -OT
Figure 2 Unknown and exposed zones in shadow-IT or -OT
In general, lack of alignment can lead to a miscommunication of priorities and a potential delay in the patching process. It is crucial for pharmaceutical companies to bridge this gap by creating a collaborative environment that encourages communication and cooperation between IT and OT teams. This will help ensure that both teams understand the importance of timely patching and the potential impact of not doing so. Moreover, it is crucial to identify shadow-IT or -OT in the pharmaceutical company and have a solid plan to move the unknown and expose it to known zones (5) (Figure 2).
Ultimately, the key to successful patch management lies in effective communication, collaboration and risk-based decision-making. By implementing these best practices, pharmaceutical companies can minimize the risk of cyber threats and ensure their safety, reliability and performance.
Develop and Test an Incident-Response Plan
Developing an incident-response plan is a must for any cybersecurity program of pharmaceutical companies. Such a plan should provide clear guidelines on the necessary steps to take during a cyberattack. This should include procedures for reporting the incident, containing its spread, identifying the root cause and restoring normal operations. Additionally, companies must conduct regular tabletop exercises to assess the effectiveness of the incident-response plan. Such exercises help identify any gaps that may exist in the plan and allow for the refinement of procedures to ensure optimal outcomes. By doing so, pharmaceutical companies can ensure they are prepared to handle a cyberattack efficiently and effectively, ultimately minimizing damage and reducing downtime.
In the event of a cyberattack, the incident-response plan for a pharmaceutical company may include the following steps:
- Preparation: It must contain response flow, classification of incidents, description of roles and responsibilities, communication channels and technical playbooks that guide with steps to react in a specific scenario.
- Detection and Reporting: The IT, OT, network operations centers (NOC) or security operations centers (SOC) team will be responsible for detecting and reporting any suspicious activity or security incidents to the incident-response team.
- Containment and Recovery: The incident-response team will work to contain the incident, recover the data or system back to normal conditions and prevent further damage to systems and data. This may involve disconnecting affected systems from the network or shutting down specific processes.
- Eradication: Once the incident has been contained, the incident-response team will investigate the incident and determine the root cause. This may involve analyzing system logs, reviewing network traffic and interviewing employees.
- Communication and Notification: The incident-response team will communicate with stakeholders, including senior management, legal and regulatory bodies, as appropriate. They will also notify affected individuals or organizations if required.
- Post-Incident Remediation: The incident-response team will work to remediate any vulnerabilities or weaknesses exploited in the attack. This may involve patching systems, updating security controls or implementing additional security measures.
- Lessons Learned and Continuous Improvement: After the incident has been resolved, the incident-response team will conduct a postmortem analysis to identify areas for improvement and update the incident-response plan accordingly.
Pharmaceutical companies should establish an incident-response team comprising cross-functional members, including IT, security, legal, communications and business operations. The team should be trained on the incident-response plan and regularly practice response scenarios to ensure they are prepared to handle an actual attack. In addition to developing an incident-response plan, companies should establish communication protocols with third-party vendors and stakeholders, such as regulatory bodies. This will help ensure that everyone is aware of their responsibilities in the event of an attack and can coordinate effectively to minimize the impact.
Train Employees on Cybersecurity Best Practices
Employees are often the weakest link in an organization’s cybersecurity defenses. To mitigate this risk, pharmaceutical companies should provide regular training for their employees on cybersecurity best practices. This includes training on how to identify and report phishing emails, how to create strong passwords and how to use the company’s security systems correctly. Additionally, companies should conduct regular awareness campaigns to keep employees up to date on the latest cybersecurity threats and trends.
Pharmaceutical companies can also consider implementing a phishing simulation program to test employees’ readiness and awareness in detecting and reporting phishing attempts. Such programs can create a safe environment for employees to learn and practice how to respond to phishing attempts and improve their cyber hygiene, which is a company’s way of ensuring best practices for the security and handling of their networks. Companies can also offer incentives or rewards to employees who report phishing attempts or demonstrate good cybersecurity practices (Figure 3).
Subject: Urgent: Security Alert
Dear valued employee,
We have detected suspicious activity on your account and need you to take immediate action to prevent unauthorized access.
Please click on the following link to verify your identity and reset your password: [Malicious Link]
If you do not take action within 24 hours, your account will be suspended, and you will not be able to access any company resources.
Thank you for your cooperation in keeping our systems secure.
Best regards,
The IT Security Team
Conclusion
Implementing these top six essential cybersecurity best practices—conducting a comprehensive risk assessment, implementing multilayered access controls, managing encryption keys, maintaining patch management, developing an incident-response plan and providing regular employee training and awareness programs—can help pharmaceutical companies protect sensitive data and systems from cyberattacks and ensure regulatory compliance.
References
- IBM. Cost of a Data Breach Report 2022; 2022. https://www.ibm.com/downloads/cas/3R8N1DZJ.
- OWASP. OWASP Top 10:2021. owasp.org. https://owasp.org/Top10/.
- MITRE. MITRE ATT&CKTM. https://attack.mitre.org/.
- Cybersecurity & Infrastructure Security Agency. Homepage | CISA. Cisa.gov. https://www.cisa.gov/.
- Vinicius, T. Back to the Future: Learning from the Past in a Patient-Centric World, PDA 2023, New Orleans, April 3-7.



 Vinicius Tarantino is a dynamic leader spearheading the transformation of digital compliance and protection in the Life Science industry. As the head of Digital Compliance and Protection at GxP-CC, he empowers Life Science companies to overcome conformity challenges and enhance safety measures through advanced technologies. With more than 20 years of experience in IT quality assurance, compliance and security, Vinicius has built a strong reputation as an industry trailblazer. Before joining GxP-CC in Germany, he played a crucial role in developing security strategies and managing complex projects across different sectors, prioritizing compliance, quality, confidentiality, integrity and availability.
Vinicius Tarantino is a dynamic leader spearheading the transformation of digital compliance and protection in the Life Science industry. As the head of Digital Compliance and Protection at GxP-CC, he empowers Life Science companies to overcome conformity challenges and enhance safety measures through advanced technologies. With more than 20 years of experience in IT quality assurance, compliance and security, Vinicius has built a strong reputation as an industry trailblazer. Before joining GxP-CC in Germany, he played a crucial role in developing security strategies and managing complex projects across different sectors, prioritizing compliance, quality, confidentiality, integrity and availability.